Im trying to find a way to monitor packets that were send by my WoW 3.3.5 client. Also i want to be able to resend the packets that i've already sent. Just give me advice where should i start? I have no idea how to do that. From OC threads is found all game functions reversed, so i decided to test this one - > SendPacket = 0x632b50. Indeed. That is the function that sends packets. I tried sending message on the chat and started debugging the function in cheat engine. In one of the parameters i found the message that i just sent, so i know this is the correct send packet function for 3.3.5. But the thing is, i don't have clue how it works, or what parameters are being passed to it.
Here is my unsuccessul method of trying to call that function while passing parameters.
Of course this returns error. To ebp, i pass some dynamic adress that idk what it is and it keeps changing over and over again, maybe that's the cause of crash. In all cases, i have no clue wtf im doing here. I was never a good reverse engineer, but i am good programmer. Please, someone point me to a place from where i should start learning. I want to read those packets the same way i read them in WPE PRO. I will make my own program that will have large variety of tools to modify those packets, resend them X amount of times, have delay between each packet, simulate lag, and much more. In other words, a perfect exploit digger. Im tried of staying out of process like a mouse.Code:try { wowHook.InjectAndExecute(new string[7] { "push ebp", // Parameter 1(I think that's the packet in bytes that is being sent to the server) "mov ebp, [042AEE58]", // <------- that's the dynamic address of the packet that is being sent "mov ecx, [00C79CF4]", // <------- IDK WTF THIS IS, type of packet?? "mov eax, [ebp+08]", // <------ (passed to parameter 2)Some value from the packet i guess, since i suggest ebp is the packet itself "push eax", // Parameter 2(Some value from the packet i guess, since i suggest ebp is the packet itself) "call 0x632B50", // <----- (calling the function) That's the send packet function "retn" }, 0); }
Shout-Out
User Tag List
Thread: WoW packet monitoring
Results 1 to 8 of 8
-
03-12-2022 #1
 Active Member
Active Member


- Reputation
- 55
- Join Date
- Nov 2014
- Posts
- 92
- Thanks G/R
- 12/18
- Trade Feedback
- 0 (0%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
WoW packet monitoring
-
Post Thanks / Like - 1 Thanks
 Corthezz (1 members gave Thanks to dlablo for this useful post)
Corthezz (1 members gave Thanks to dlablo for this useful post)
-
03-12-2022 #2
 Active Member
Active Member


- Reputation
- 55
- Join Date
- Nov 2014
- Posts
- 92
- Thanks G/R
- 12/18
- Trade Feedback
- 0 (0%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Ok, so i found this github GitHub - TrinityCore/WowPacketParser: World of Warcraft Packet Parser
This guy did amazing amount of work. However, version 3.3.5 is not listed here... does anyone have packet parser for 3.3.5? I need to take look at the source code to at least get an idea how it works....
-
Post Thanks / Like - 1 Thanks
 Corthezz (1 members gave Thanks to dlablo for this useful post)
Corthezz (1 members gave Thanks to dlablo for this useful post)
-
03-12-2022 #3
 Contributor
Contributor


- Reputation
- 98
- Join Date
- Aug 2015
- Posts
- 147
- Thanks G/R
- 38/61
- Trade Feedback
- 2 (100%)
- Mentioned
- 1 Post(s)
- Tagged
- 0 Thread(s)
I tried diving into packets myself a while back and it gets very tricky - very quickly.
My knowledge at the moment still isn't the greatest but hopefully it'll give you a few starting points.
Firstly, if you're wanting to edit / replay packets you need to understand your position or at least your goal.
there are two main ways of doing this either in-process when you're injecting into the client hooking the packet function and editing the info just before the client sends it.
or the proxy method :
https://www.youtube.com/watch?v=iApN...l=LiveOverflow
YMIR (trinity's packet parse) - they use NPCAP to track and read all the packets, however having the binary of each packet isn't very helpful as they are all encrypted.
At the moment I have no idea how to decrypt these packets - after speaking to the guys at trinity for a bit they hinted at the fact that you need to find the session key (in memory) that is generated on login. This is some how used in the decryption of packets.
You also won't find the source for YMIR as they've decided to keep it closed source in fear of people selling the source or blizzard patching it.
Another useful note might be understanding blizzards network infrastructure :
Network Serialization and Routing in World of Warcraft
That's about as far as I got before I got bored :P
Best of luck mate, keen to see what you come up with !
-
Post Thanks / Like - 1 Thanks
 Corthezz (1 members gave Thanks to Dupheadss for this useful post)
Corthezz (1 members gave Thanks to Dupheadss for this useful post)
-
03-13-2022 #4
 Active Member
Active Member


- Reputation
- 55
- Join Date
- Nov 2014
- Posts
- 92
- Thanks G/R
- 12/18
- Trade Feedback
- 0 (0%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Wait wait, i don't need to decrypt the packages. I only wish to be able to see them just like in WPE PRO.
This is exactly what i aimt to achieve
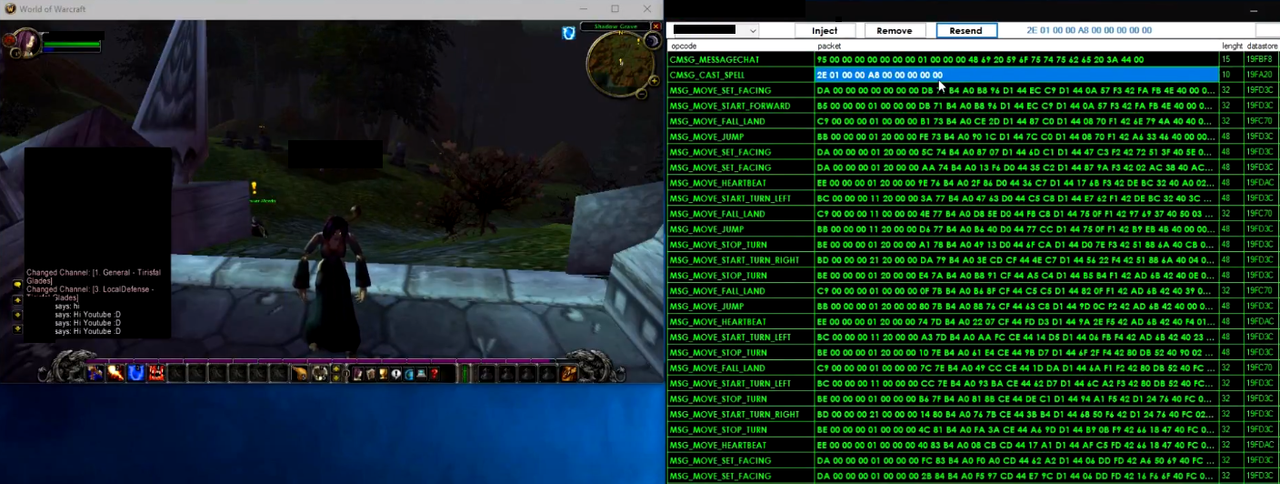
This is a friend of mine. Unfortunately i can't ask him to help me with this, obviously it's a lot of work. Is this your definition of encrypted packets? Because that's the way i want them to look like. I am able to read those bytes that were recorded, i just can't get to the point of getting them.
I also don't want to do it outside the client or just modify it before it is sent(If that was the case then i would just use WPE PRO). I want to be able to send the same packet as many times as i want. For that purpose i should only hook my stuff with the game function which i just cannot reverse. What i do know is if i can send a custom packet trough the game, then i can record all packets that go trough this function. For example for every incoming packet the goes trough the function, i can modify the function and allocate new memory where i will temporarily store the packet, and then i can use memory reader to read that packet and just display it in my table, after that clear the allocated memory and prepare it to record the new packet.
So all i should know is how to send a packet using the in-game function, do you have any knowledge of that? Anyway, thank you so much for your post.
-
Post Thanks / Like - 1 Thanks
 Corthezz (1 members gave Thanks to dlablo for this useful post)
Corthezz (1 members gave Thanks to dlablo for this useful post)
-
03-13-2022 #5
 Active Member
Active Member


- Reputation
- 55
- Join Date
- Nov 2014
- Posts
- 92
- Thanks G/R
- 12/18
- Trade Feedback
- 0 (0%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Update
game version wotlk 3.3.5, 12340
function SendPacket = 0x632b50,
Code:datastore = ?? dynamic address packetSize = datastore+0x10 packetInBytes = datastore+0x4
I found it, there is the packet
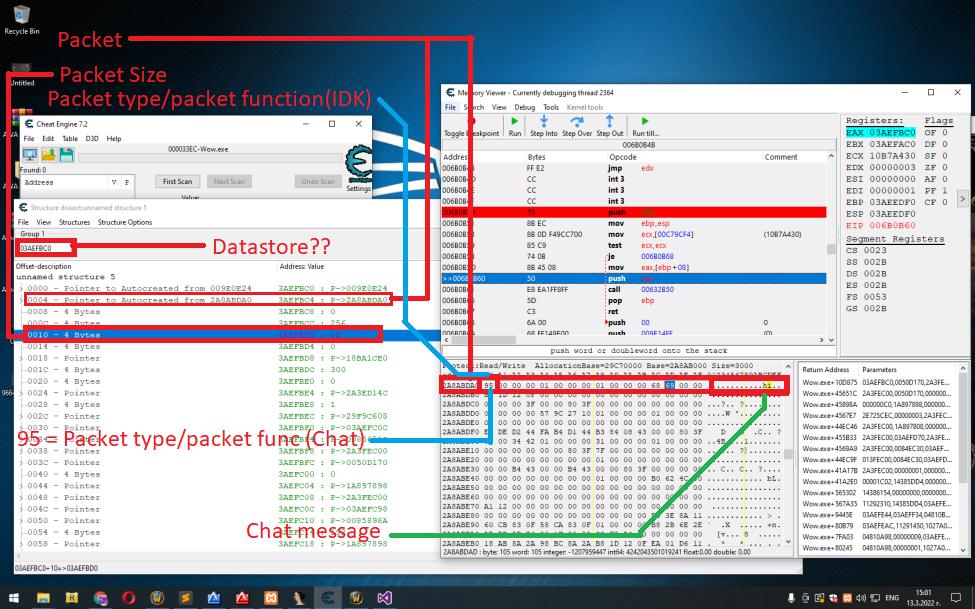
So yeah i can record the outgoing packets. In this original function i can put some asm to copy the packet bytes and store them in temporary new allocated memory that i will refresh on every outgoing packet. And then display them in a list. I got some other things missed from the puzzle. I have no idea how to call the send packet function manually and send the already recorded packet. I just have no clue what input i should pass to the parameters without crashing wow. Once i get my hands on those two things, record & re-send, what will follows is a large tool with huge library to modify the packets. A perfect exploit digger. There is never a perfect private server or thing from this kind. There is allways a hole, and i aim for the perfect way to find that hole. I'm sure i can even crash the server if i find the proper script that doesnt have the proper checks. If someone can understand what he sees in the picture i've shown please correct me, point me to the right direction if you can. I know how annoying it is to help noobs from time to time, but i do help my friends with some stuff. So i believe karma should reward me in some way and make someone reply to this post ? XD
Jokes aside, just tell me if i am wrong with the stuff i described in the picture, and which offsets should i use to correctly record the packet. Right now the address that i call datastore, is address that contain address to the packet, packet's size, and some other stuff that i don't know wtf is. Also the datastore addr is dynamic. If it is dynamic, i don't know how im gonna call the send packet function because i obviously can't pass dynamic address to it. Thank you for your time.Last edited by dlablo; 03-13-2022 at 10:06 AM.
-
Post Thanks / Like - 1 Thanks
 Corthezz (1 members gave Thanks to dlablo for this useful post)
Corthezz (1 members gave Thanks to dlablo for this useful post)
-
03-13-2022 #6
 Legendary
Legendary


- Reputation
- 658
- Join Date
- Sep 2008
- Posts
- 1,023
- Thanks G/R
- 7/215
- Trade Feedback
- 0 (0%)
- Mentioned
- 8 Post(s)
- Tagged
- 0 Thread(s)
Not sure if it will help, but this sounds like it may be relevant: GitHub - tripleslash/wowscout: Real time packet analysis and modification tool for World of Warcraft 1.12.1, 2.4.3, 3.3.5 and 4.3.4.
-
03-13-2022 #7
 Active Member
Active Member


- Reputation
- 55
- Join Date
- Nov 2014
- Posts
- 92
- Thanks G/R
- 12/18
- Trade Feedback
- 0 (0%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Yes, thats the alternative of the tool that i want to make. However, my tool will be more rich in options, and again - undetected. I plan to use it on my main account so i must develop it step by step. Also i'm not sure how detected this guy's tool is. I'm not aware of the anti-cheat state of my server either.
Also, i got update.. i was super retard to search for the datastore pointer when he was in front of me the entire time.
Now i got the full description of the input that i must pass when i call the send packet function, however... i must admit that i never injected asm code in my life so = D... pray for me
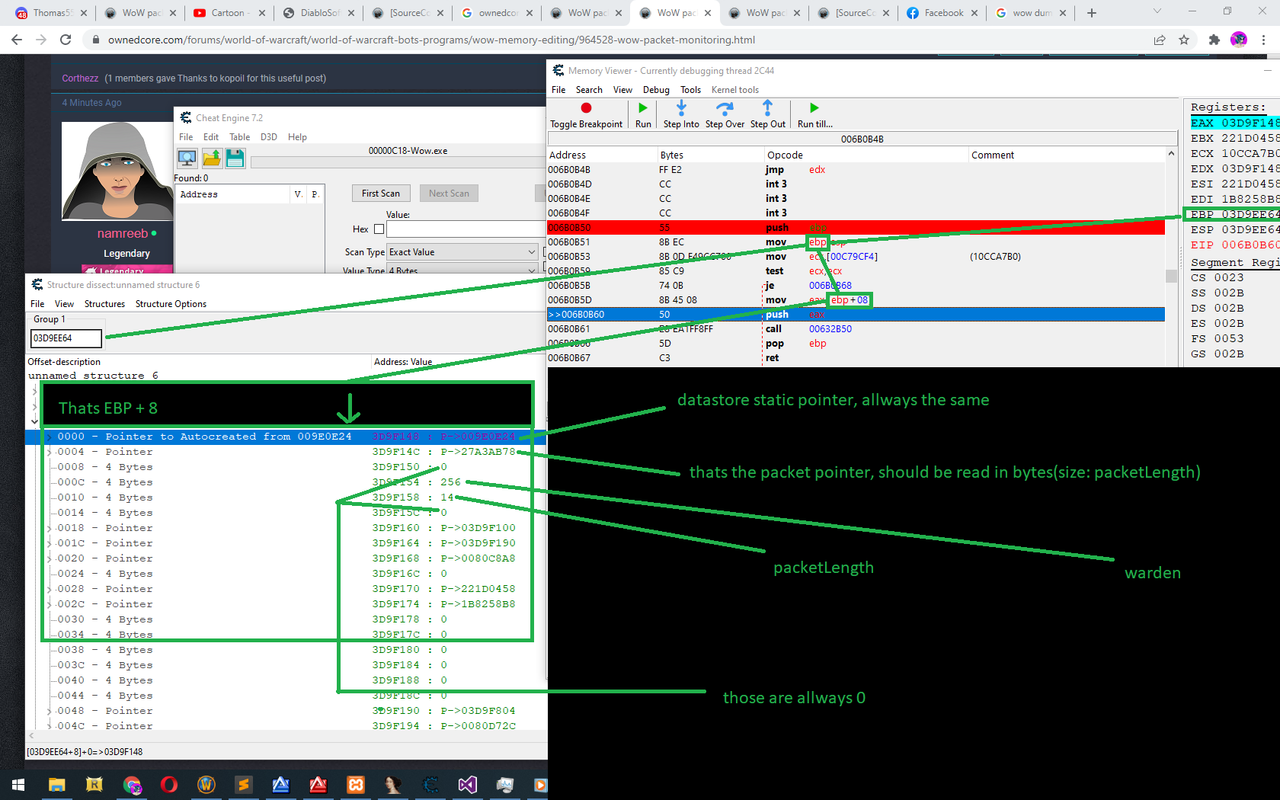
EDIT: I'm done, packet monitoring + packet send is done. Again, as allways, i managed to do the stuff while evading the warden. Above i provided you with enough info about the packet structure, sadly i can share no more. My first asm script ever executed, was successful.Last edited by dlablo; 03-13-2022 at 09:52 PM.
-
06-05-2022 #8Member

- Reputation
- 1
- Join Date
- Aug 2019
- Posts
- 8
- Thanks G/R
- 0/0
- Trade Feedback
- 0 (0%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Hey man, I have also started the same journey as you but unfortunately I am stuck understanding the send packet wrapping function at 0x632b50
What does this datastore pointer you mentioned mean? Also, did you manage to craft and send a packet by yourself? What are the parameters of the sendpacket function at 0x632B50?
First one is the this pointer but the second one changes with the different type of packet and I could not find anything useful with it : void __thiscall SENDPACKET(int this, int a2) - the a2
2022-06-05 17_47_502-Window.png
Similar Threads
-
[python] wow packet logging proxy
By argh44z in forum WoW Memory EditingReplies: 15Last Post: 09-21-2011, 11:25 PM -
WPE Cannot detect WoW packets
By popinman322 in forum WoW Bots Questions & RequestsReplies: 0Last Post: 07-01-2010, 12:46 PM -
[C] WoW packet decryption
By pendra in forum WoW Memory EditingReplies: 12Last Post: 03-06-2010, 12:39 AM -
packet monitoring
By lanman92 in forum WoW Memory EditingReplies: 17Last Post: 12-17-2008, 12:55 AM -
WoW packets.. where are they?
By Stretch in forum World of Warcraft GeneralReplies: 0Last Post: 01-28-2007, 01:54 PM













